Everything About Military-Grade Encryption
Here, we have enlisted all the segments that we have covered in this article. You can click on the link below to easily move to the relevant section. Be assured, we have broken the concept of encryption in lucid terms so anyone can understand what it’s all about.
The Basics
Before we understand what exactly is military-grade encryption, let’s first go through the basics of encryption. In simple terms, Encryption means scrambling of information in such a way that it looks like gibberish. When you enter your credit card details on a website, it encrypts the data. That means, it converts the plaintext into something called ciphertext through advanced cryptographic algorithms. It makes the data unreadable and uncrackable. This way, your data remains safe on the internet while transmitting from one server to another.
So, who can decipher the data? Only the entity that holds the key to the cipher. The key is the most important part of an encryption process and how and where a service provider stores it (more on this later), makes all the difference. So to sum up, encryption is a process of encoding information into unreadable ciphers which can only be accessed by parties that hold the key.
So What is Military-Grade Encryption?
Simply put, Military-grade encryption means AES-256 encryption. AES stands for Advanced Encryption Standard that has a 256-bit key size. There are many types of encryption such as SHA-256, RSA-2048, AES-256, etc. AES-256 is one of the popular encryption methods because of its fast and reliable cryptographic method. Up until now, no computer or human has been able to crack an AES-128-bit key, let alone an AES-256 encryption key.
AES-256 is an encryption method that uses symmetric cryptography, meaning, it uses the same key for both encryption and decryption. Due to this fast approach, VPNs, banks and messaging apps rely on AES cryptography for faster encryption and decryption. Now coming to the difference between AES 128-bit and 256-bit encryption method. When we say, it’s 128-bit encryption, it means that the key needed to decrypt the data is 128 bit in size and it has 3.4 x 10³⁸ possible key combinations that run into 39 digits. Similarly, the 256-bit key has 1.1 x 10⁷⁷ possible key combinations and the key runs into 78 digits long. With such a humongous figure, any supercomputer would need billions of years to crack the key which is simply impossible.
To conclude, when a VPN company says it offers Military-grade encryption then it means you are getting AES 256-bit encryption which is simply unbreakable. Keep in mind, even 128-bit and 192-bit encryption are considered military-grade, but companies generally offer 256-bit to tighten your security even further.
Is Military-grade Encryption a Marketing Gimmick?
Many cybersecurity experts believe that military-grade encryption is a marketing gimmick and it’s milked by companies by associating online security with the military’s high standard. In my opinion, it’s true to some extent. As we saw in the above section, even AES 128-bit encryption is secure enough and it’s simply unbreakable. Not to mention, AES 256-bit encryption is not something new and exclusive as companies generally tout.
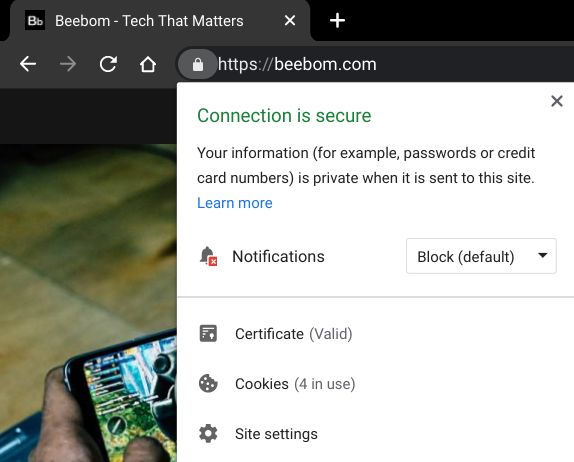
Even an HTTPS website that you open on a web browser already supports military-grade encryption. If you see a padlock icon next to the URL then AES 256-bit encryption is turned on by default. All the information transmitted between you and the website remains private. Not even your ISP can snoop on the data. Security researchers explain that on the encryption side of things, AES 256-bit encryption is more than enough. Instead, users should focus on where the company is storing the keys and what protocol it’s using to transport the keys. And that’s where end-to-end encryption comes into play. You should not just fall for military-grade encryption (because you already have it) and should find where the keys are stored.
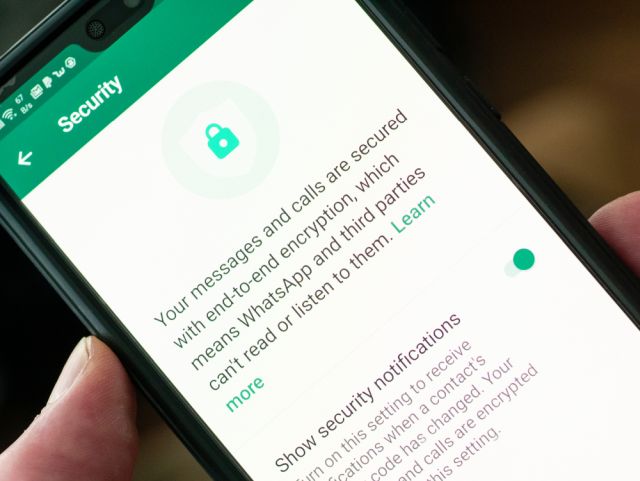
On WhatsApp and Signal, the decryption keys are stored with the sender and the recipient. Similarly, Zoom was earlier storing the keys on its server, but with end-to-end encryption enabled on Zoom, the keys will rest with the host and the participants. So all I would say is look for end-to-end encryption wherever possible because you are already getting military-grade encryption by default– on apps, websites, browsers, and online services.
Military-grade Encryption Explained For You
So that is all about the much-touted military-grade encryption that companies advertise endlessly. While it’s a simple phrase that inspires confidence, the truth is that you are already covered by military-grade encryption, by default. In fact, Google started deranking websites in 2018 that were still on the old HTTP protocol so there is a high possibility that you are browsing the web securely. Anyway, that is all from us. If you found the article helpful then do comment down below and let us know.